Plant Security
CONSULTATION | ANALYSIS | PENETRATION TESTING
Ensure plant safety from a security perspective too
As digitalization and automation grows, technical safety alone is no longer sufficient. Nowadays, systems must also be protected against access by unauthorized third parties. Possible cyber-attacks on technical systems must be considered and integrated into safety management. However, plant safety and security are currently largely separate disciplines with highly specialized service providers which naturally bears certain risks.
CSE-Engineering has therefore combined both disciplines in the integrated concept of Plant Security. This makes IT and OT security a natural part of the plant safety concept. With us, you have a specialized partner for the entire plant security management.

Contact
Marius Baechle, M.Sc.
Process Safety Engineer
phone_in_talk +49 721 6699 4709
email Send an Email
CSE Managing Director Prof. Jürgen Schmidt is a member of the Commission for Plant Safety (KAS), which advises the Federal Ministry for the Environment, Nature Conservation and Nuclear Safety. This commission published a guideline (KAS 51) on measures to prevent unauthorized interference in 2009. The guideline serves to protect against serious dangers caused by cyber-attacks or drones and serves to fulfil the requirements of the Security Verification Determination Ordinance (SÜFV).
In cooperation with 8com GmbH (IT-Security), CSE-Engineering has founded the innovation center CESIS, which aims to combine safety and security considerations of IT/OT systems in order to provide complete security for safety-oriented process control technology. Together with renowned manufacturers and operators, procedures are defined which make the current standards and regulations (NA 163, KAS 51, etc) practicable.
Required Documents:
The following information and documents are required for project work in Plant Security:
- Specification of the process
- Operating conditions | states
- P&ID flow diagrams
- Hazard and risk assessment (e.g. HAZOP)
- PCE component list
Optional:
- Previous safety | security concepts
- Overview of the IT infrastructure
Consultation
Consulting on national and international security standards: IEC 61508/11, ISO 27000, ISO 62443
Analyses
Weak point analyses and penetration tests for plants and plant components.
Safety Management
Establishment of a functional safety management system in accordance with the latest regulations (NA 163, KAS 51)
Result
Depending on the defined targets, you will receive a plant security concept individually adapted to your plant. In this the results of the vulnerability analysis by penetration tests are shown and state of the art countermeasures are recommended for your system. In addition, the influences of the countermeasures on the performance of your system are considered and optimized in order to achieve maximum security and efficiency. A comprehensive security report, containing a detailed explanation of the individual points of execution, is produced to complete the project.
Project duration
The duration of the security analysis depends on many different factors, such as the system sizes, the equipment used (sensors, actuators, controls, etc.) and of course on the scope of your requested project (penetration test, security management, etc.). Therefore, a meeting is held at the beginning of the project to discuss your needs and requirements. Based on this we estimate the time required and provide you with a detailed offer.
Standards, publications, manuals
CSE-Engineering provides Functional Safety according to the state of the art. For this purpose we use national and international regulations, publications and our many years of experience.
Standards
- IEC 61511/08
- ISO 27000
- ISO 62443
- NA 163
- KAS 51
- BSI
Publications | Manuals
- Prof. Dr.-Ing. Jürgen Schmidt: Plant Security – Public Awareness and Mitigation of Third Party Attacks as a new Layer of Protection in the Safety Concept. Chemical Engineering Transactions, Vol. 77, 2019.
Trainings & Coaching
With the Applied Safety seminar program of the CSE Academy you can also make your employees fit for functional safety – for example with the seminar PCT safety devices. Also as in-house training.

Request by e-mail:
Note:
By using this form, you agree that your data may be stored within the framework of the Privacy Policy of the CSE-Engineering Center of Safety Excellence for the duration of the processing.
Plant Security Basics
Fundamentals
Are protective devices allowed to become intelligent? Should we also use the possibilities of digital transformation in safety engineering? Due to the constant digitalization and automation, these questions are becoming more and more popular in the industry. One example of the combination of safety technology and Industry 4.0 are the model-based online safeguards, which allow plants to be operated more safely and at the same time more economically. However, they are also vulnerable, e.g. via people, networks, sensors or maintenance tools. Cybercrime is therefore affecting more and more plants and the topic of cybersecurity is becoming increasingly important.
In order to establish this cyber security, two guidelines have been published in recent years: NA 163 and KAS 51, both of which aim to support the operators of safety instrument systems in minimising the risk of a cyber-attack using state-of-the-art technology. Both approaches provide a good basis, but cannot be applied generally or define concrete measures to minimise the risk. Therefore, there is still a high demand for supporting the implementation of the guidelines in the companies. To enable this, a brief overview of the two guidelines follows:
Brief description of the NA 163:
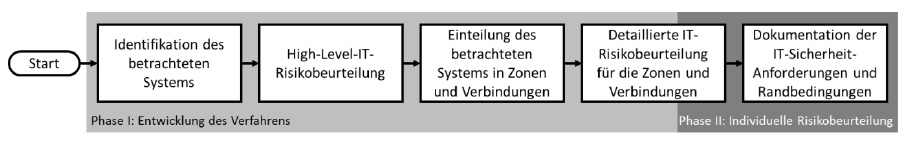
The procedure according to NA 163 is divided into two phases:
Phase I: Development of the process
Phase II: Individual risk assessment
The steps of the first phase are carried out once as an example of a system defined within NA 163. Other cases, e.g. when the safety and operation control share the CPU, are not included and reduce the applicability of the NA 163. However, if the defined system is available, all elements of the system under consideration are covered in the first point. Subsequently, threats to the integrity of the PCT safety check, coming from the manipulation/destruction or theft of the elements, are recorded and evaluated.
An assessment of availability or confidentiality, which also contributes to the general security objectives (Confidentiality, Integrity, Availability) is not considered here. The next step is to define measures to counter the threats in an appropriate manner and finally to check whether the defined measures have been effectively implemented.
The last step, the verification of the implementation of the measure and the documentation, must be run through individually for each element of the safety instrument system to be assessed and thus forms phase II.
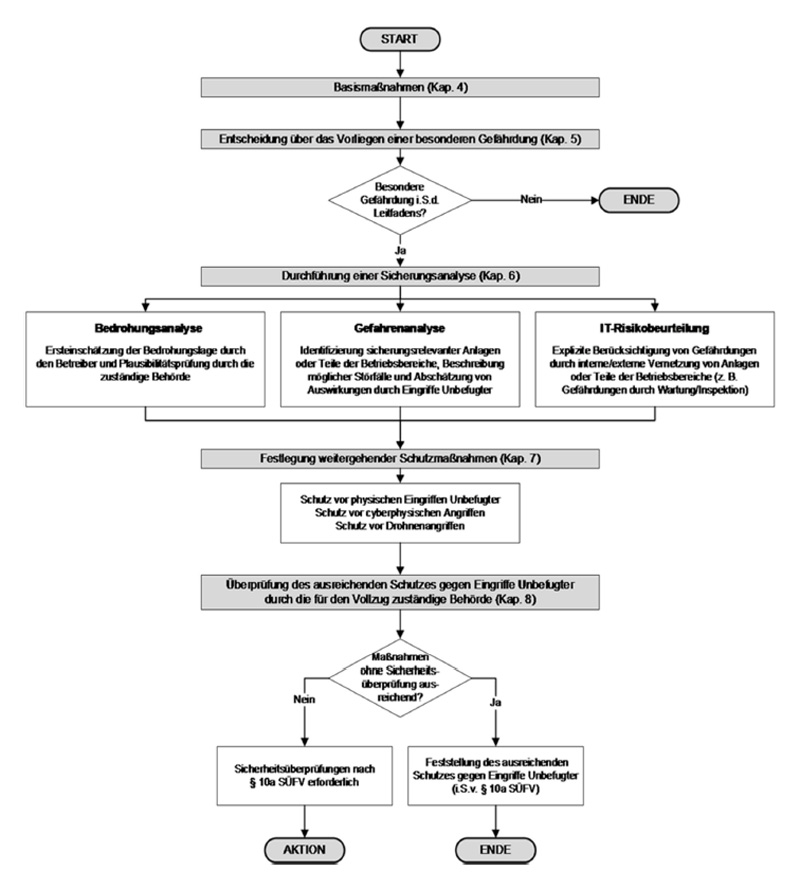
Brief description of KAS 51:
In the first step, general basic measures are defined which are to be implemented by all operators of operational areas, irrespective of whether a particular hazard exists with regard to a serious risk. In the latter case, a safety analysis must be carried out, which consists of three parts: threat analysis, hazard analysis and IT risk assessment.
The threat analysis investigates the extent to which the facilities or the environment appear particularly attractive to unauthorised intervention. The purpose of the hazard analysis is to determine whether unauthorised intervention could lead to a particular hazard within the meaning of the guidelines in which case a serious danger must be assumed. The last step, the IT risk assessment, deals with the IT threats based on weak points in your system and assesses its risk. Depending on the risk, further protective measures can then be defined. Whether the organizational or technical measures taken are sufficient to protect the operation against interference by unauthorized persons is assessed by the responsible authority based on the evaluation of the operation, and marked on the security report. The necessity of security checks in accordance with SÜG, and in conjunction with § Section 10a SÜFV must be based on the organisational and technical measures implemented with regard to the risk reduction achieved.